RevEng
Hi, so am doing some research on some free vpns, and in one of them found a random google drive url, that downloads a "pu.pj" file. While the internet says .pj files belong to a nintendo64 emulator, I am not able to use it to open the pj-file. The contents of the pj- file is a 4608 long of ASCII characters. Which i've tried to decode but dont seem to be able to. However, the Linux command "file -C pu.pj" does give a bunch of strings, but it contains a bunch of random stuff, im not sure what to make of it. Anyone able to help me pinpoint this? (ill re-upload if necessary) The contents of "pu.pj" here: https://paste.centos.org/view/953ab256 The contents of "file -C pu.pj" here: https://paste.centos.org/view/abfbdefc
cross-posted from: https://slrpnk.net/post/8481443 I am currently investigating and reverse engineering **free** VPNs for a master thesis, and just came across something I thought I'd share. Not sure if I'll name-drop the VPN that this code is from, but it's not the one mentioned within the hardcoded links... Nor do I encourage visiting any of the links in the screenshot. I'm sharing this as a warning as to never use free vpns! They are most often the opposite of what they promise to be. (by free I do not mean the free versions of premium services). But either way; be careful about your VPN choice, as they have access to a lot of sensitive data. I'm sure most peeps here know of this already, but next time you hear someone using a free vpn, let them know... This first image/code was sitting inside a file called NetworkModule, with some hella weird external links. 1. addrDOTcx, seems to have been linked to malware? Comes up flagged as malicious a few times on [VirusTotal](https://www.virustotal.com/gui/url/095636b57c1246e28fbbfce6016802a76bae5216bf48bfbfa27c7581906b8d97). 2. freevpnDOTzone, seems to be another free possible malicious VPN service, might investigate this one later. 3. bigbrolookDOTcom, seems to longer be a registered domain. But wtf? Was this VPN service linked to p*rn?? ::: spoiler IMAGE HERE; Don't visit these links unless you know what you're doing. 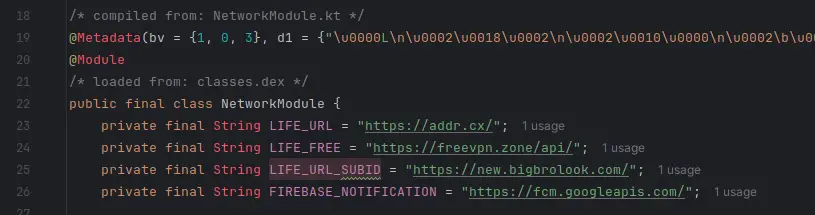 ::: Furthermore, there is this interesting find; Now I am no expert coder, frankly quite the amateur. But does the below code really mean what I think it does? Seems like it could be creating a fake connection?  Is used once here;  Stay safe 🌻 >edit: formatting
 cloud.binary.ninja
cloud.binary.ninja
Is binja cloud abandoned? I liked the idea of a shared database, especially for CTF problems but it doesn’t really seem like the cloud option is supported. Apparently it was for ML training data for binja but I haven’t seen any new features related to ML in binja either…
Improvements! - Debugger:LLDB. Upgraded SWIG-generated Java (plus docs) to LLVM/lldb 16.x. (GP-3442, Issue #5359) Decompiler. Added an option to the Decompiler, controlling the maximum size of jumptable that can be recovered. (GP-3266) - Decompiler. Improved Decompiler function call-override to consider calling convention when differentiating function signatures. (GP-3268, Issue #5335) - Decompiler. The Decompiler now respects tool options for shortening template strings within symbol names. (GP-3369) - Importer:ELF. Added Max Zero-Segment Discard Size import option to ELF Loader. Value was previously hard-coded to 255 bytes. (GP-3428, Issue #5273) - Importer:Mach-O. Restored Mach-O indirect symbol creation when binding information is not present, such as when importing a DYLIB extracted from a dyld_shared_cache. (GP-3526) - Languages. Added windows__stdcall calling convention as an alias to the default calling convention for aarch64 and x86-64. (GP-3472) - Scripting. Improved the RecoverClassesFromRTTIScript recognition of special vtables when they are in memory blocks not tied to imported file bytes. (GP-3463) - Scripting. Mitigated a RecoverClassesFromRTTIScript issue where mangled typeinfo names were not always getting extracted from memory when more than one bad data type was created over the memory containing the mangled string. (GP-3467)