appsec
Found this interesting list: https://list.latio.tech/ On the open source side, there is https://www.dependencytrack.org/

If you're interested in a way to implement Zero Trust principles like least-privilege access or make your access policies more granular without creating code bloat this is something to check out. Cerbos Hub externalizes application permissions (RBAC/ABAC) and makes it easier to write and maintain fine-grained access policies without falling into a slow doom spiral of spaghetti code. You write your policies in a central repo, and deploy as many containerized policy decision points as you need alongside the relevant services in your application. Policy checks are an API call. No single point of failure or lag issues. You can maintain and monitor distributed policy decision points from one place. Make changes in Hub once and the changes are deployed everywhere. It supports PDPs deployed in serverless environments, at the edge or on device. There's a collaborative policy playground to write and test your policies. It has a central audit log of all the policy decisions that take place across your application.
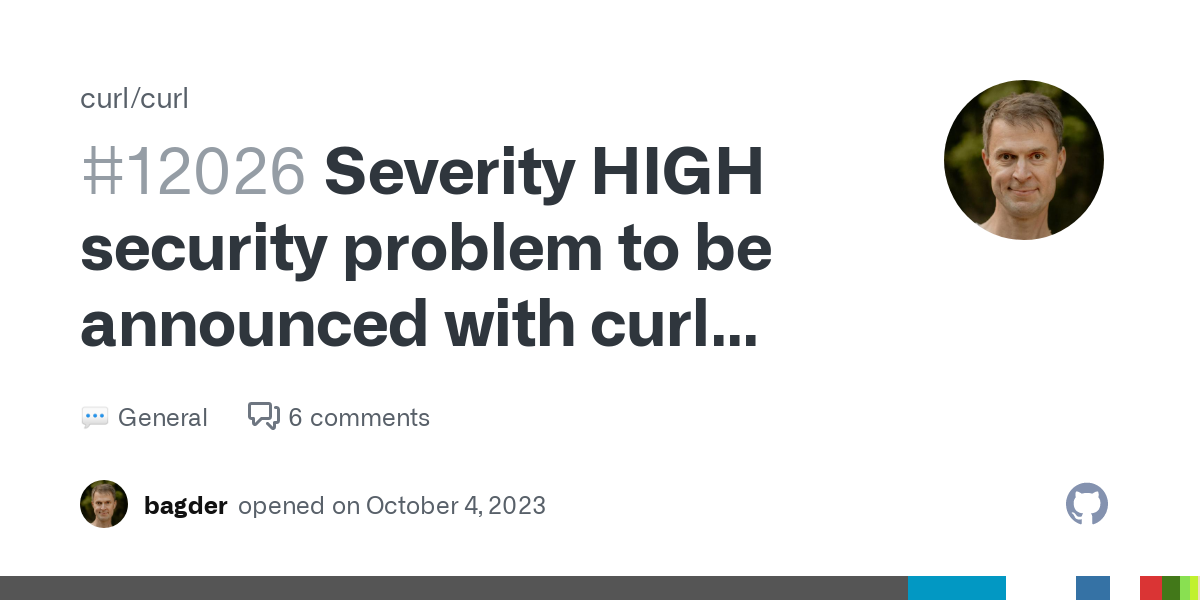
cross-posted from: https://infosec.pub/post/8123190 > Hello everyone, > > > I work in appsec, my manager would like to send us to a conference this year. We are based in Europe, and the company would like to across intercontinental travel. > > I have OWASP Global 2024 in Lisbon on my radar, as well as the BlackHat EU in London, is there any other conference you guys would recommend?
 blog.solidsnail.com
blog.solidsnail.com
 blog.solidsnail.com
blog.solidsnail.com
cross-posted from: https://infosec.pub/post/5707149 > I talk about a report I've made to MSRC in the beginning of the year regarding vscode. > > It's a bit different. There's no in depth technical stuff, because I basically just reported the feature, not a bug.
 blog.trailofbits.com
blog.trailofbits.com
By Artem Dinaburg eBPF (extended Berkeley Packet Filter) has emerged as the de facto Linux standard for security monitoring and endpoint observability. It is used by technologies such as BPFTrace, Cilium, Pixie, Sysdig, and Falco due to its low overhead and its versatility. There is, however, a dark (but open) secret: eBPF was never intended…
 github.com
github.com
PoC for CVE-2023-4911. Contribute to leesh3288/CVE-2023-4911 development by creating an account on GitHub.
elttam is an independent security company providing research-driven security assessment services. We combine pragmatism and deep technical insight to help our customers secure their most important assets.
The scenario is this: a brand new Ubuntu 22.04 server has an account which is restricted to running sudo logrotate *. Can we get root? Short answer: Yes. I couldn’t find much online about this type of exploitation of logrotate, so let’s document something for future use.
On September 27, 2023, the U.S. National Security Agency (NSA), the U.S. Federal Bureau of Investigation (FBI), the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the Japan National Police Agency (NPA), and the Japan National Center of Incident Readiness and Strategy for Cybersecurity (NISC) released a joint cybersecurity advisory (CSA) detailing activities of the cyber actors known as BlackTech. For a description of this report, see People's Republic of China-Linked Cyber Actors Hide in Router Firmware. Cisco has reviewed the report. Cisco would like to highlight the following key facts: The most prevalent initial access vector in these attacks involves stolen or weak administrative credentials. As outlined in the report, certain configuration changes, such as disabling logging and downloading firmware, require administrative credentials. There is no indication that any Cisco vulnerabilities were exploited. Attackers used compromised credentials to perform administrative-level configuration and software changes. Modern Cisco devices include secure boot capabilities, which do not allow the loading and executing of modified software images. For more information on secure boot, see the Cisco Trustworthy Technologies Data Sheet. The stolen code-signing certificates mentioned in the report are not from Cisco. Cisco does not have any knowledge of code-signing certificates being stolen to perform any attack against Cisco infrastructure devices. These key points align with the Cisco consistent stance and messaging that advises customers to follow best practices as described in the Cisco blog post: Attackers Continue to Target Legacy Devices. Modern network infrastructure devices now contain numerous security features and capabilities that mitigate the aforementioned attacks. The Cisco Secure Development Lifecycle (SDL) applies industry-leading practices and technology to build trustworthy solutions that have fewer field-discovered product security incidents. As part of our ongoing commitment to network reliability, Cisco has recently launched an effort focused on network resiliency. For more information on this effort, see the Cisco Network Resilience portal. This advisory is available at the following link:https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-csa-cyber-report-sept-2023
 www.checklyhq.com
www.checklyhq.com
Checkly Director of Engineering Daniel Paulus take a deep dive into DNS debugging in his latest post for the Checkly blog.
 blog.securelayer7.net
blog.securelayer7.net
A new WinRAR vulnerability, CVE-2023-38831 could allow attackers to take control of your computer so it's important to take action now
 socradar.io
socradar.io
Using the open source programs/platform, anyone can scan millions of public buckets at once using certain keywords. Typically, buckets...
I’ve recently been looking into iRacing, which is an online racing simulation video game.
 blog.isosceles.com
blog.isosceles.com
Early last week, Google released a new stable update for Chrome. The update included a single security fix that was reported by Apple's Security Engineering and Architecture (SEAR) team. The issue, CVE-2023-4863, was a heap buffer overflow in the WebP image library, and it had a familiar warning attached: "Google
*x-posted from [/r/netsec](https://old.reddit.com/r/netsec/comments/16m3kqg) by [/u/arrowflakes](https://old.reddit.com/u/arrowflakes)*
Due to a recent Google change, MFA isn't truly MFA.
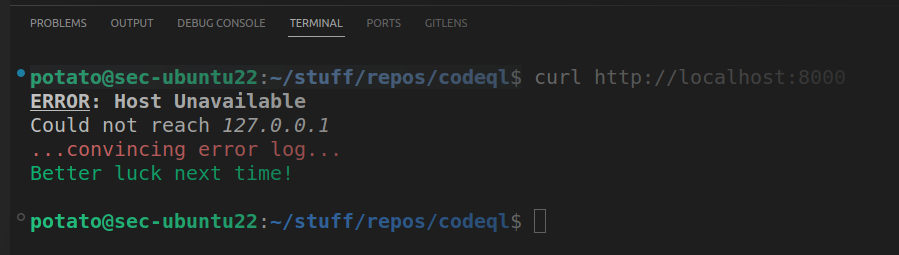
Introduction When fuzzing large-scale applications, using a single server (even with 4 64-core AMD Ryzen CPUs) may not be powerful enough by itself. That’s where parallelized/distributed fuzzing comes in (i.e. automatic sharing of results between fuzzing systems). In this guide, we’ll take a look at how to set up multiple servers fuzzing the same program using AFL++, linked all together with an NFS (Network File System).
*x-posted from [/r/netsec](https://old.reddit.com/r/netsec/comments/16l167p) by [/u/yqopmin](https://old.reddit.com/u/yqopmin)*
*x-posted from [/r/netsec](https://old.reddit.com/r/netsec/comments/16kwvfl) by [/u/AsahiLina](https://old.reddit.com/u/AsahiLina)*
blog post about A Big Look at Security in OpenAPI
*x-posted from [/r/netsec](https://old.reddit.com/r/netsec/comments/16kb5dq) by [/u/keissiaresa](https://old.reddit.com/u/keissiaresa)*
 engineering.fb.com
engineering.fb.com
Meta’s Native Assurance team regularly performs manual code reviews as part of our ongoing commitment to improve the security posture of Meta’s products. In 2021, we discovered a vulnerability in …
 symantec-enterprise-blogs.security.com
symantec-enterprise-blogs.security.com
*x-posted from [/r/netsec](https://old.reddit.com/r/netsec/comments/16hr0ul) by [/u/nareksays](https://old.reddit.com/u/nareksays)*
 www.sonarsource.com
www.sonarsource.com
Our Research team discovered critical code vulnerabilities in Proton Mail, Skiff, and Tutanota. This post covers the technical details of the XSS vulnerability in Skiff.
 deform.co
deform.co
Today, the telegram channel of the infamous darknet forum reported that hackers had broken into the infrastructure of Datadvance and its pSeven platform,
This is my first write-up, on a vulnerability I discovered in iTerm2 (RCE). Would love to hear opinions on this. I tried to make the writing engaging.